Reduce the exposure surface of your business
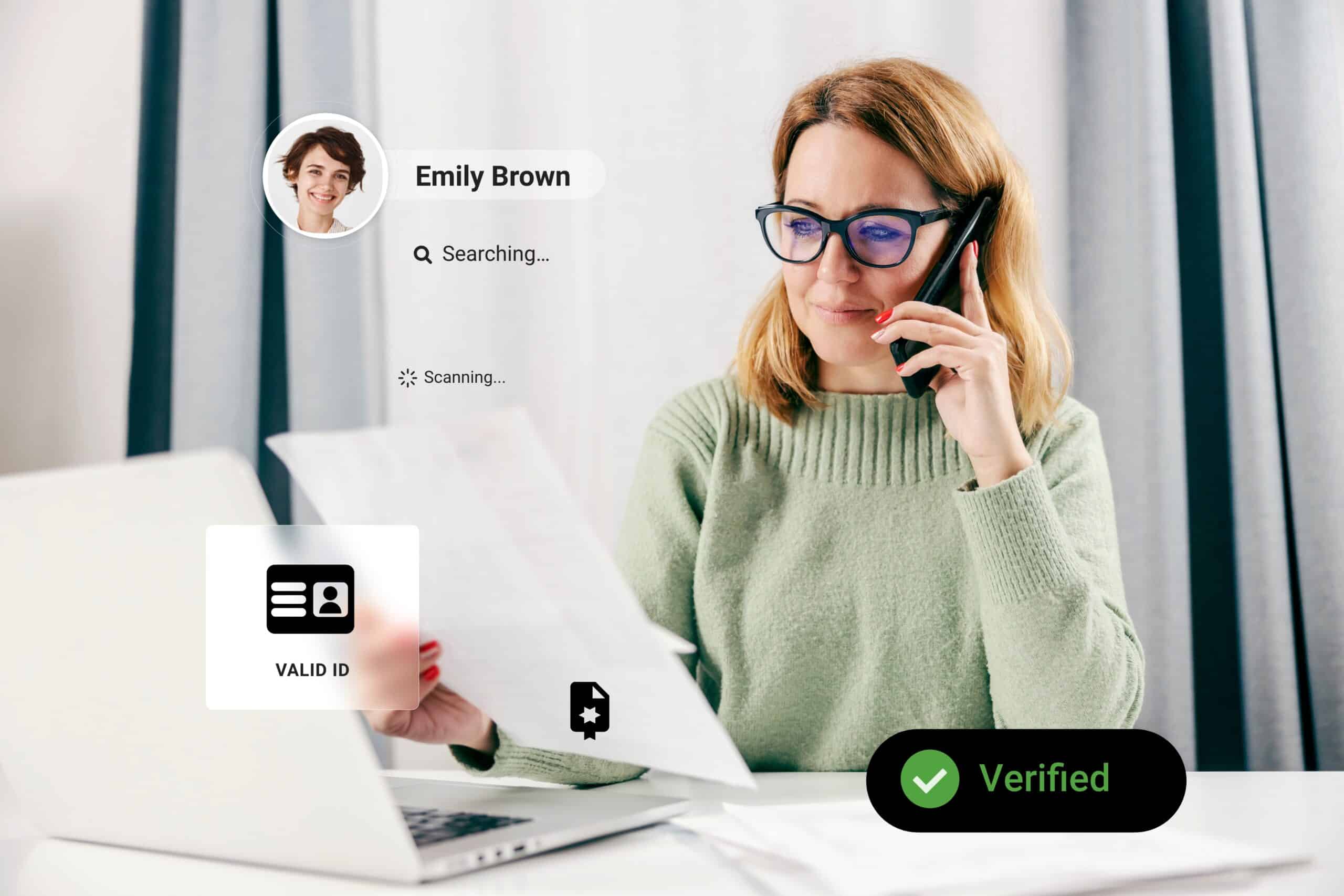
As the digital age speeds up, businesses like yours collect, store and process vast amounts of sensitive digital information. The more information you accumulate, the greater your surface exposure for cyber attack.
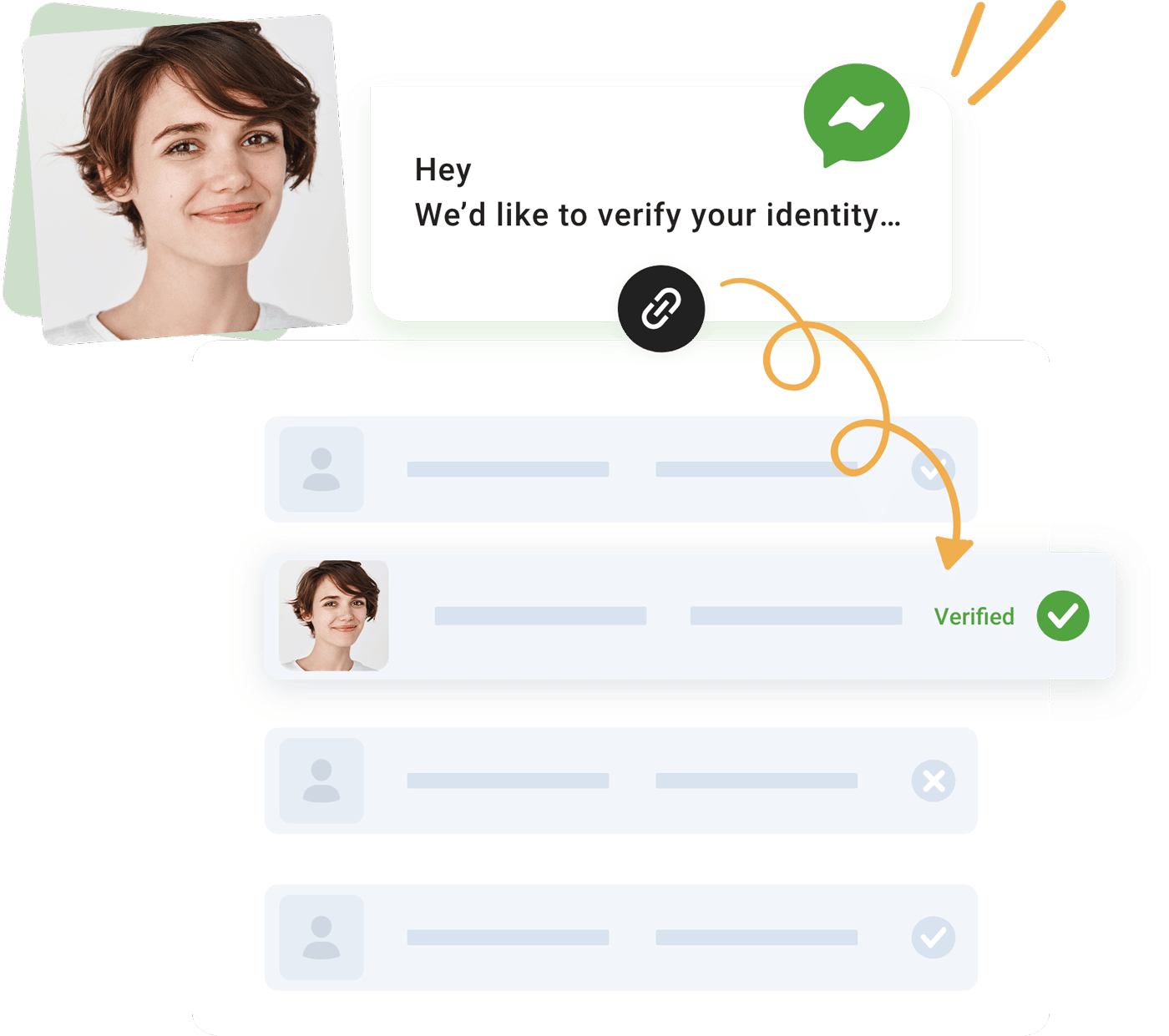
Too often, when senior executives take a closer look at their security practices, they discover alarming vulnerabilities, like the use of email to collect sensitive data from customers.
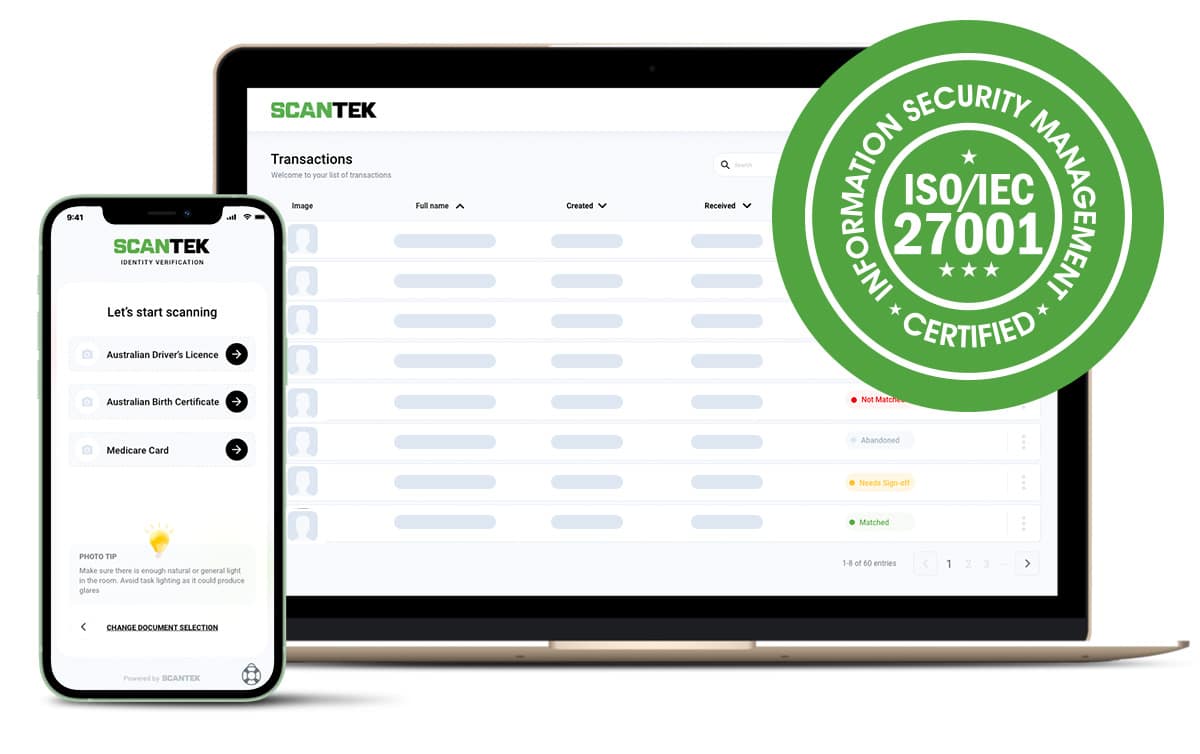
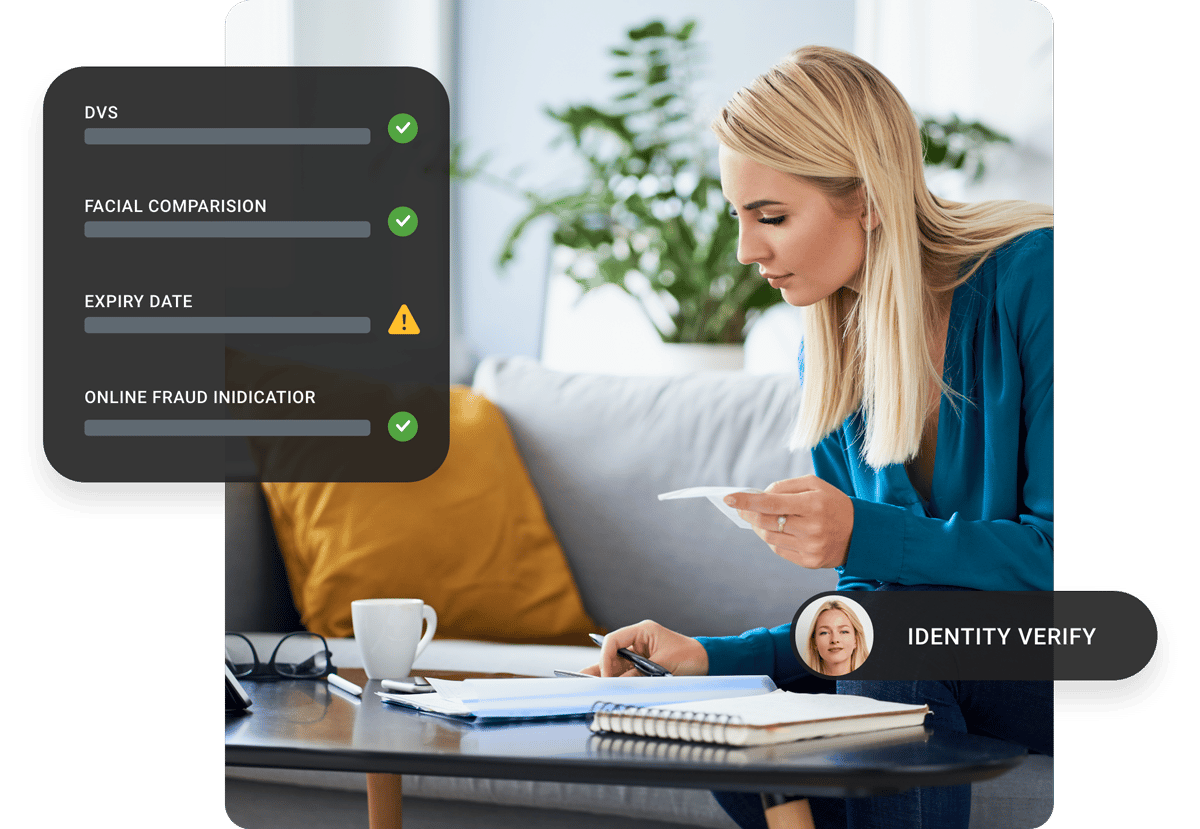
Fortunately, it is possible to have heavy-duty information security that works: ISO provides tried-and-tested standards of practice, proven to shrink risks to your business, so that you don’t need to lose sleep at night.