Data Security and Privacy
Scantek’s multi-tier security protects your business from cyber-attacks and data breaches
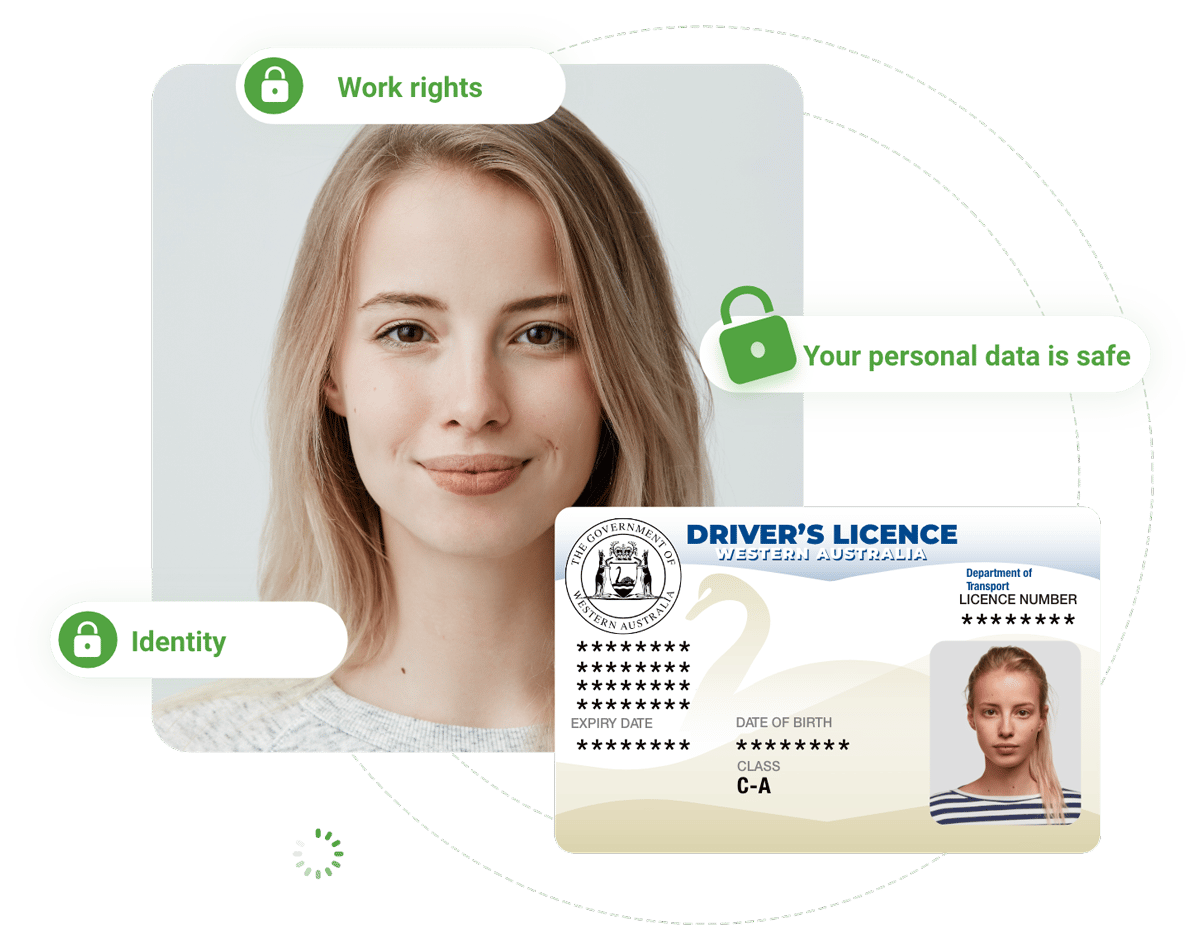
For over a decade, we've been tightening our heavy-duty data security posture to safeguard your business.
We know scammers will do anything to get private customer details, so data security is one of our highest priorities. Our main focus is to safeguard you from insider threats and human error, as they are two of the leading causes of data breaches.
We maintain the gold standard in information security by layering policies, processes, and controls to shield your systems and verification data: ISO 27001 compliant, specialist security designers, multi-tier security architecture

The concerning truth about digital data storage
The digital transformation in recent years has seen many more businesses gain online accessibility. The creation and hosting of valuable data online has increased significantly, encompassing personal identity information (PII), trade secrets, and intellectual property.
Scams to access that data are becoming more sophisticated. Even large companies become prey to them due to their high level of sophistication.
Now, more than ever, it’s important to guarantee the protection of personal information collected from your customers.If you can’t, you risk data breaches that expose your customers to potential harm. That’s damaging to your brand and your reputation, too.
You need data security that both you and your customers can trust.
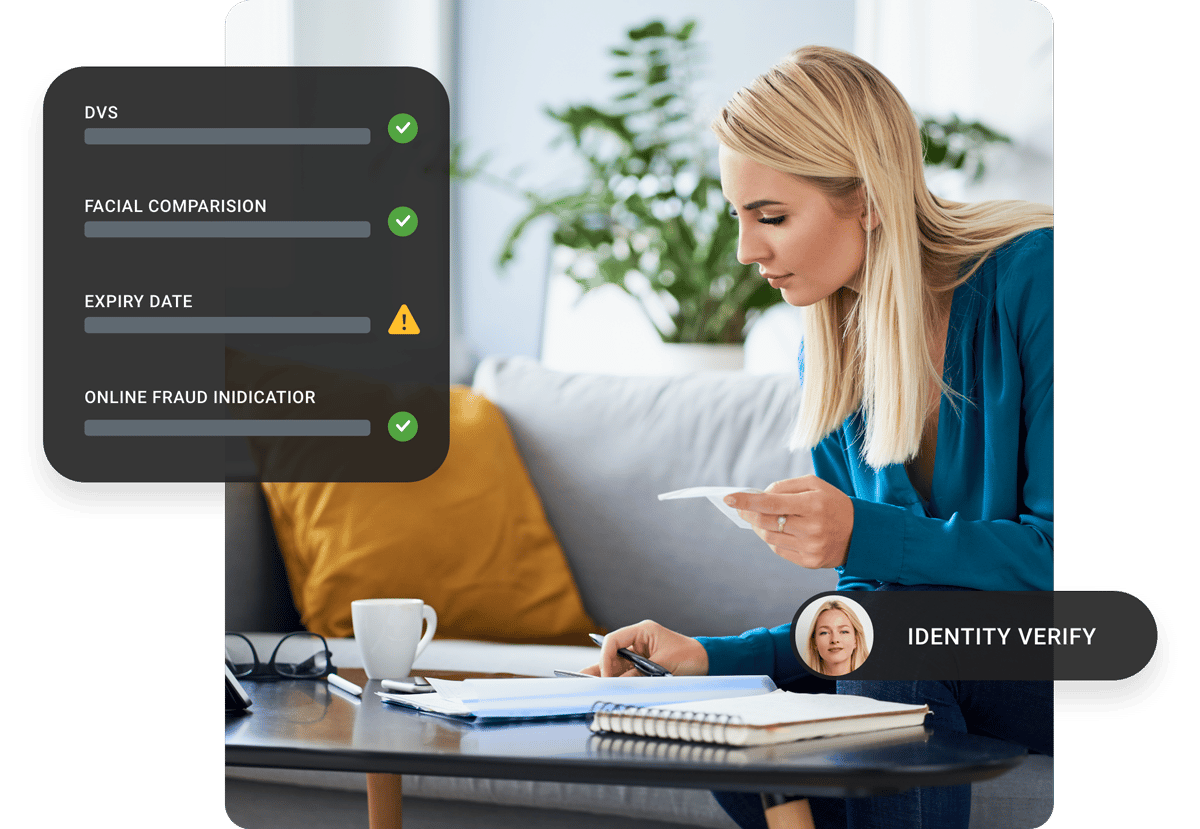
What’s best practice in data security?
Bulletproof infrastructure and technology
Cybercriminals dig for weak spots in your security framework. To prevent access to sensitive customer information, you must have an advanced digital environment that can keep up with a rapidly changing landscape.
Scantek’s digital infrastructure has multiple layers of security built on zero-trust and privileged access principles.

Specialist insight and design
Trustworthy security infrastructure requires experts to build it. Architects need advanced knowledge to design storage systems that will withstand multiple cyberattacks. The infrastructure must also stay up-to-date with emerging trends in cybersecurity.
Scantek’s specialists lead the way in secure digital verification.

Security that never falls asleep
It isn’t enough to simply have good infrastructure. Your security must remain unbreached for the entire lifecycle of the data and then be safely disposed of when no longer needed. Keeping data for longer than needed creates unnecessary risk.
Scantek can store data for as little as 28 days (for example, in venue entry verifications) or as long as 9 years (required for banking, financial services, and insurance (BFSI) compliance). After that, it’s permanently deleted.
By using our technology, you can actively track where crucial data is located and analyze its usage patterns, ensuring that there are no blind spots when it comes to managing the information within your purview.
How Scantek protects your data
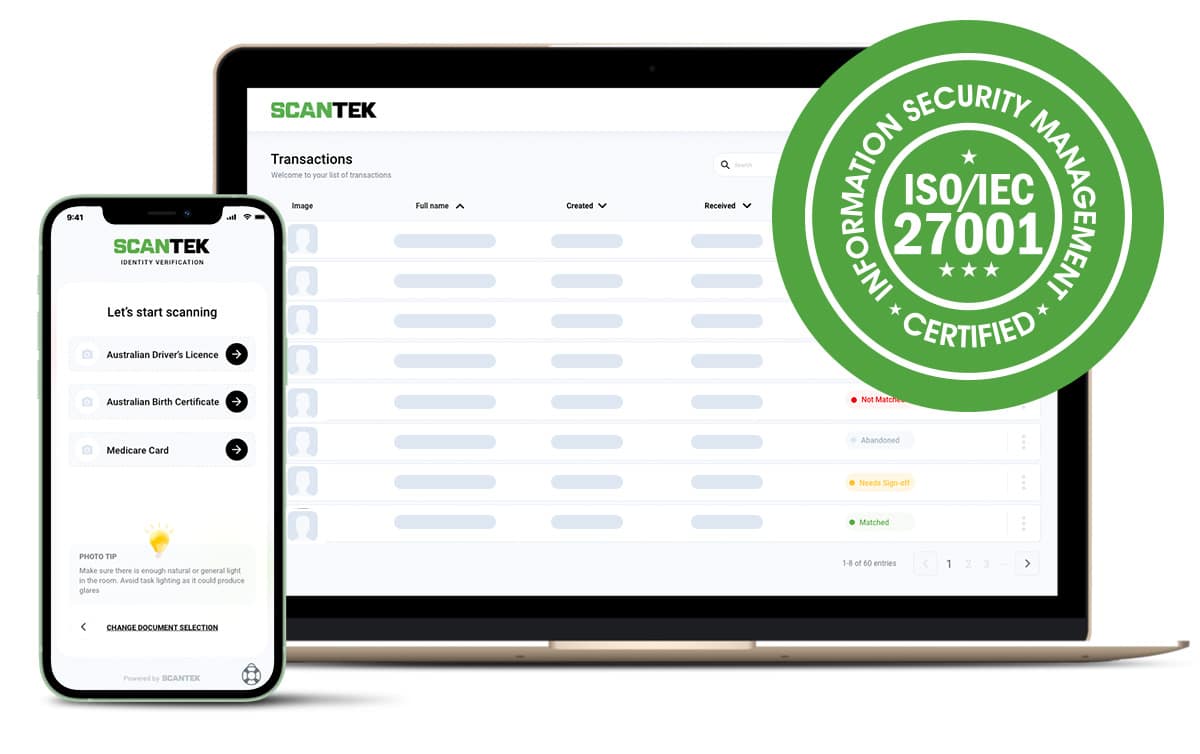
1. ISO 27001 - Information security management
Our ISO 27001 compliance means we provide the highest level of data protection and privacy in Australia. Formally known as ISO/IEC 27001:2013 Information Security Management, it’s the leading international standard on information security.
We’ve maintained compliance since 2018, and we’re externally audited every year to ensure we uphold best practices on:
- Confidentiality: only authorized people have the right to access information.
- Integrity: only authorized people can change the information.
- Availability: the data must be accessible to authorized people whenever needed.
2. Multi-tier security
Scantek uses a multi-tier cloud-based security architecture. It’s like the bank vault of cyber security—every ‘door’ on every level (network, transport, or database information) needs a different key. This multi-level design minimises the surface area for a possible cyberattack.
3. No unauthorised access
- Vulnerability scanning across our systems and servers
- Intrusion prevention and detection software
- The principle of least privilege—access is on a right-to-know basis
- Multi-factor authentication, with access tokens expiring every 30 seconds
4. Data never leaves Australia
We don’t host any databases offshore, where data protection laws differ, secure network connections are not guaranteed, and technology standards fluctuate. We use data centres across Sydney, Australia, to ensure an environment we can control, secure, and monitor.
5. Encryption at rest and on the move
Why Scantek?
When you do digital security the right way, it’s far safer than manual methods. Hundreds of Australian businesses already trust us because our squeaky-clean track record is over 10 years old.
We practice what we preach
Since our business is about keeping you safe, we’re meticulous about verifying our own staff. As part of our industry compliance, we train all Scantek employees to be security aware. We work within strict confidentiality bubbles, applying zero-trust and privileged access principles to our own business.
Trusted by Australian businesses
Data security is nothing new to us. It was a priority from the day we started because of the sensitive nature of information that verification requires. Since then, our security layers have grown more sophisticated. In over a decade, no criminal activity has breached our security.
Trailblazing technology
Scantek employs leaders in the fields of data science and technology. We thrive on innovation, so you’ll often find us in think tanks, chipping away at our next breakthrough on tools or technology. Innovation and expertise ensure the data we protect on your behalf is safe, even as frauds evolve their tactics.
That’s one of the reasons we’re trusted by hundreds of Australian businesses today. Our tried-and-tested technology has earned us a reputation for being the safest digital verification technology in the country.

Ready to get started?
Our identity experts are available to talk through your requirements, answer questions and set up a demo.